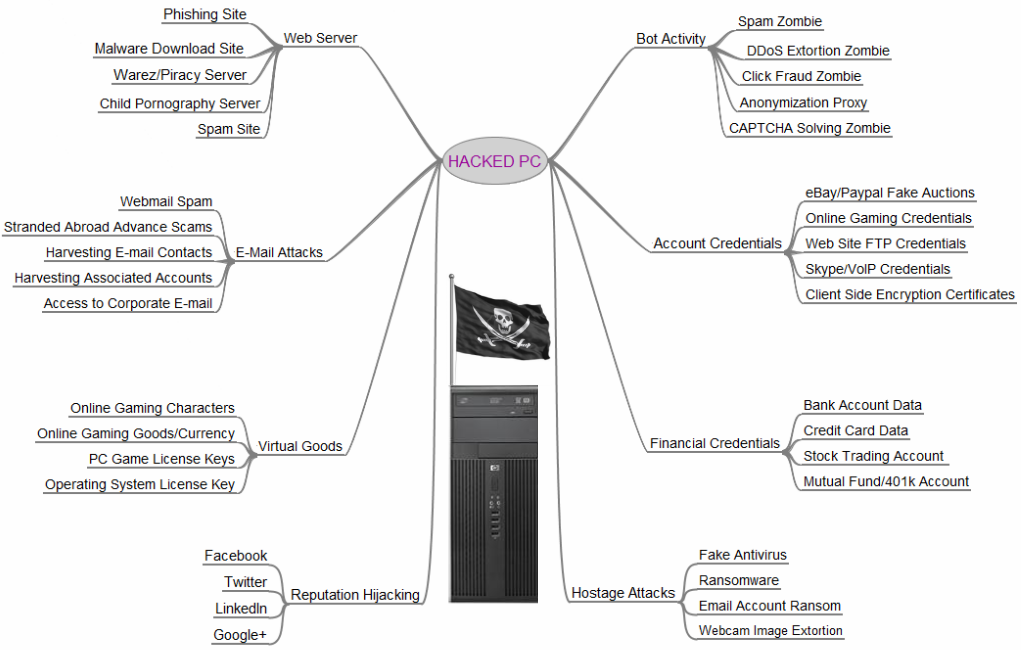
I’ve recently been writing mail server software that detects whether the remote is a compromised PC sending spam (frequently the case) versus a legit mail server whose connection should be permitted. The quantity of hijacked PCs is staggering, which made this article all the more interesting:
http://krebsonsecurity.com/2012/10/the-scrap-value-of-a-hacked-pc-revisited/